Cryptography is a fundamental element in cyber security, but it’s not always easy to explain how different encryption methods work. In the Apply Music module of our STEM EDA curriculum, students are introduced to several historical encryption methods. While secure at the time of their invention, these methods are all but obsolete now; however they still work as fun activities to engage your students as well as teach them cryptography fundamentals.
One such activity is called the Cipher Disk. It’s a simple 2-circle dial system that encrypts messages letter by letter (or substitution). This activity is found on pages 49-52 in the Apply Music module. Each student will need:
- scissors
- a brad
- markers
- pages T50-T51 from the Apply Music Teacher Manual
1. Cut out the circles on pages T50-T51.

2. Place a brad through the center of the two circles, connecting them with the smaller circle on top.
3. Around the outside of both circles, write out the alphabet, one letter in each wedge from A-Z.

4. You should now have 2 alphabet disks attached in the middle that can freely spin on the brad.
5. Decide which letter you want to shift your alphabet to and rotate your cipher disks appropriately. For example, if you shift A to U, your shifted disks will align as in the picture below.
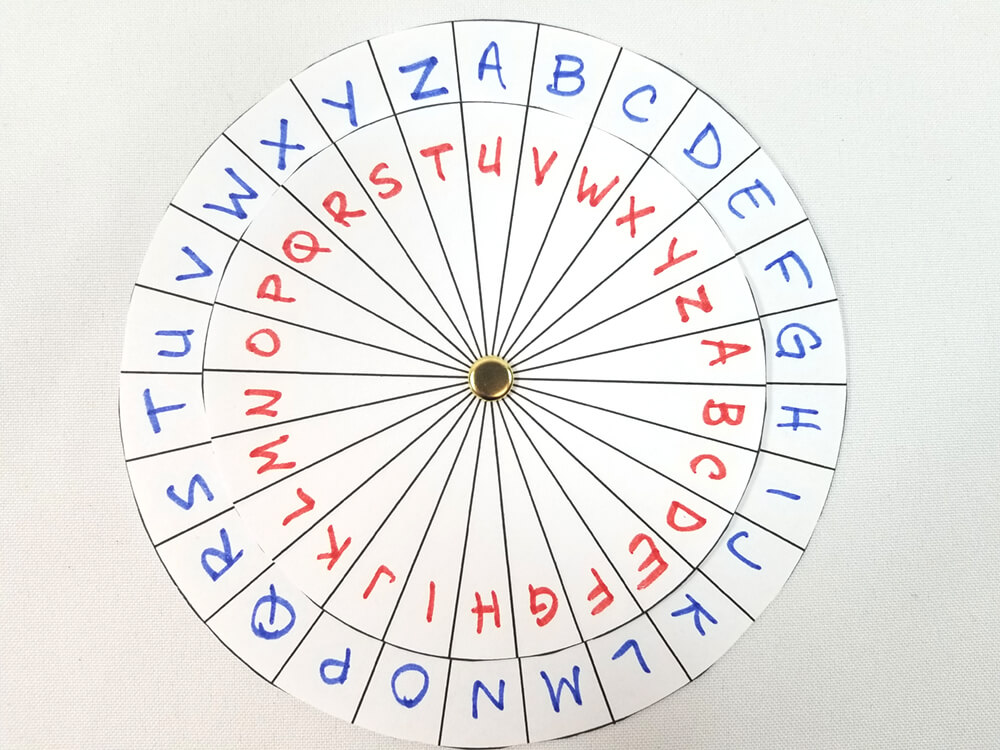
6. Use page 51 to write the original message you wish to encrypt. When encrypting your message, you want to read from the inside circle to the outside circle (for consistency’s sake). Using the earlier shift of A to U, the message “I AM AN AGENT OF HARP” would be rendered “C UG UH UAYHN IZ BULI.”
7. To decrypt a message using the same method, the person reading the message would need to know what the shift is (A to U) and then would be able to translate the message back into English by taking the encrypted letters and reading their shifted cipher disk outside to inside.
This easy activity is a great hands-on way to introduce middle schoolers to the concepts of encryption and decryption and to start conversations about cyber security. There are pages provided in STEM EDA to practice recording messages and encrypting them with different shifts and then passing the messages to someone else to decrypt the message. Have fun!
BONUS CHALLENGE: Challenge your students to create a message, pass it on, and decrypt the message – without knowing the shift.
If you would like to know more about this activity or learn more about the context for the students as they explore cryptography, check out our STEM EDA curriculum or request access to NICERC’s free curricula.